I would use a tool like winscp to copy the file over the network, but the error indicates you have another problem with your haproxy config potentially because the haproxy service won't start.
thank you for the answer!
I've been working on this for over 10 hours,
I can get the file out,
A friend of mine made the system work like a win98 
Even after installing the certificates, I get a browser error
please help
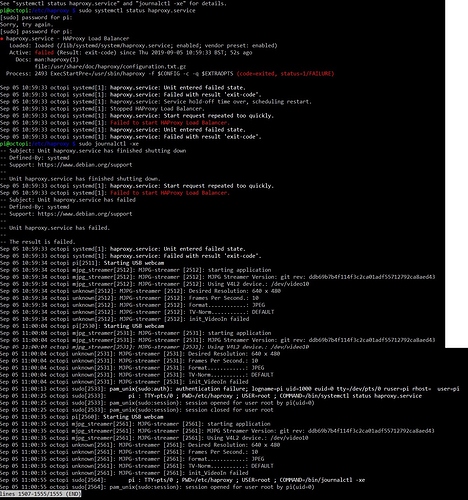
Have you tried the systemctl and journalctl command as the error message suggested?
Thanks for the answer!
I really don't know what that means,
What should I check?
Type
sudo systemctl status haproxy.service
and
sudo journalctl -xe
(the things you get es error message after you used sudo service haproxy restart)
It could show you where the problem is
Yeah that didn't really help.
I think best is you post the inside of your haproxy.cfg and maybe somebody sees an error there. I'm not quite familiar with haproxy and hoped these commands would give us an easy solution.
Btw there are several undervoltage warnings - are you sure that your power supply for the pi is sufficient?
A charger is not a power supply.
Do you think this creates the problem in haproxy.cfg?
I've seen insufficient power cause all kinds of issues on RPis. Misread configs. Network disconnects. Garbled data on the serial. Malformed responses. Mayhem.
But if you don't get an undervoltage warning it's probably not the reason. Still - a charger is not a power supply.
So the haproxy.cfg file looks correct, so the only thing that I can think of that may be causing haproxy to not work properly would be the certificates themselves. Are they actually there where you are specifying them in the cfg file? For example, if you followed the instructions exactly your ca-file should be /home/pi/ssl/OctoPrintCA.crt. And remember in linux systems capitalization does matter.
You're right. I just fixed that in the original post. The path to the ca-file was incorrect.
What does your haproxy.cfg contain?
speed-pro.ml.pen might should be speed-pro.ml.pem
The file names have to match...
Thank you're right.
I fix this and there is no error in sudo service haproxy restart.
I'm installing the username1.p12 and OctoPrintCA.crt certificate,
Still getting browser error, test on chrome and explorer
Hi Octopi’ers,
I may be in the minority, but I am not using OctoPi to control my printer. It’s been a while, but a few years ago when I set OctoPi up, it was not able to control Ultimaker printers properly. It had something to do with header gcode needed. So I ended up using OctoPi strictly for webcam access. I used it with DDNS, HTTP (not S) and port forwarding with a static IP on my Pi to monitor print status. I never really considered it dangerous since the USB/printer control part was simply not in use.
Recently I thought “hey I should upgrade OctoPi” so I did and now I MUST login to even use the webcam. Maybe someday I can control the printer and these security measures would be more relevant to me. In the mean time, I have a few simple questions:
-
Can I set up guest access not requiring authentication on current releases of OctoPi? I could give a sh*t if some unscrupulous hacker watches my prints.
-
What about Let’s Encrypt for SSL certificates? This seems like a more robust way to get free SSL certificates that are not based on self-signed domains. Typically HTTP (non-SSL) is needed for occasionally renewing the certificate, but Apache can be restricted to only allow non-SSL access to very specific URLs needed for this purpose.
Or if anybody has better ideas for dumb non-authenticated webcam access not requiring OctoPi, I’d be open to that for now!
fyi, if you just want to install your own certificate, just to access octopi via https (without client certificate)
after downloading your certificate from your preferred certificate authority
merge certificate and key into one file
cat ssl-cert-XXX.com.crt ssl-cert-XXX.com.key > ssl-cert-XXX.com.pem
make sure in the pem file that the end of the certificate, and the start of the private key are on different lines
-----END CERTIFICATE-----
-----BEGIN PRIVATE KEY-----
copy the cert and bundle in the certs directory
cp ssl-cert-XXX.com.pem /etc/ssl/certs/
cp ssl-cert-XXX.com.ca-bundle /etc/ssl/certs/
edit the haproxy.cfg file
vi /etc/haproxy/haproxy.cfg
change
frontend public
bind :::80 v4v6
bind :::443 v4v6 ssl crt /etc/ssl/snakeoil.pem
to
frontend public
bind :::80 v4v6
bind :::443 v4v6 ssl crt /etc/ssl/certs/ssl-cert-XXX.com.pem ca-file /etc/ssl/certs/ssl-cert-XXX.com.ca-bundle verify none
how you should be able to access your octipi using https://octopiDNSname.com/
It may be worth noting that octopiDNSname.com is within a public top-level domain like .com rather than something within .local.
that was just an example, but yes, the certificate i installed was a sectigo/comodo wildcard certificate for a '.com' top-level domain. ... well technically, it is for a subdomain.
A lot of people attempt to bind a certificate to octopi.local or similar.