What is the problem?
Using nginx as a reverse proxy, when reverse proxying HTTPS on a non-standard port, there is no way to get Octoprint to respond with the appropriate CSRF port.
The main problem seems to be that X-Forwarded-Port is not respected, and when X-Forwarded-Proto is used it overwrites the ports used for CSRF.
What did you already try to solve it?
I've done some pretty extensive research into CSRF and nginx, and followed ideas from Reverse proxy configuration examples
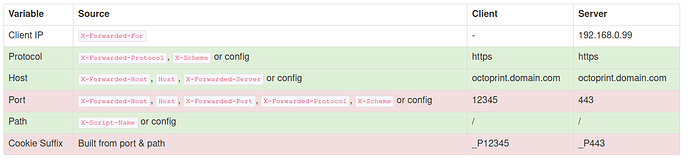
Configurations I have attempted include almost every combination of commenting and uncommenting the below proxy_set_header lines. The below configuration results in the attached screenshot (edited domain).
server {
listen 12345 ssl;
server_name octoprint.domain.com;
gzip off;
ssl_certificate /letsencrypt/live/domain.com/fullchain.pem;
ssl_certificate_key /letsencrypt/live/domain.com/privkey.pem;
ssl_session_cache shared:SSL:10m;
ssl_protocols TLSv1.2;
ssl_ciphers HIGH:!aNULL:!MD5;
modsecurity on;
modsecurity_rules_file /etc/nginx/conf/modsec.conf;
add_header Strict-Transport-Security "max-age=31536000; includeSubDomains" always;
proxy_buffering off;
client_max_body_size 10G;
location / {
proxy_pass http://192.168.0.21/;
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
#proxy_set_header X-Scheme $scheme;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_set_header X-Forwarded-Scheme $scheme;
#proxy_set_header X-Forwaded-Host "octoprint.domain.com";
#proxy_set_header X-Forwaded-Host "octoprint.domain.com:12345";
proxy_set_header X-Forwaded-Host $host;
#proxy_set_header X-Forwarded-Port 12345;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_http_version 1.1;
proxy_set_header Upgrade $http_upgrade;
proxy_set_header Connection $http_connection;
#proxy_set_header Authorization $http_authorization;
#proxy_set_header X-Forwarded-Ssl on;
#proxy_pass_header X-CSRFToken;
}
}