What is the problem?
Accessing octoprint (on octopi) via an nginx reverse proxy (with auth basic) on a separate machine fails to connect and gives this message in the Chrome developer tools:
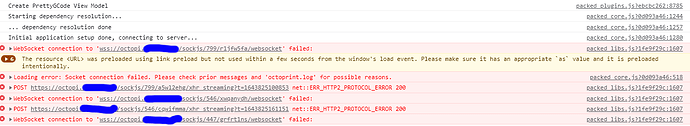
packed_libs.js?1fe9f29c:1607 WebSocket connection to 'wss://octopi.######/sockjs/799/r1jfw5fa/websocket' failed
What did you already try to solve it?
Lots and lots of different variants of nginx configuration, after following guides including Reverse proxy configuration examples and various other similar requests for help on the web.
Logs (syslog, dmesg, ... no logs, no support)
Interestingly, the octoprint log shows that the connection is appearing:
2022-02-02 18:09:39,144 - octoprint.server.util.flask - INFO - Passively logging in user myusername from 192.168.3.111
2022-02-02 18:09:39,145 - octoprint.access.users - INFO - Logged in user: myusername
2022-02-02 18:09:41,849 - octoprint.server.util.sockjs - INFO - New connection from client: 192.168.3.111
2022-02-02 18:10:41,978 - octoprint.server.util.sockjs - INFO - New connection from client: 192.168.3.111
2022-02-02 18:11:42,142 - octoprint.server.util.sockjs - INFO - New connection from client: 192.168.3.111
2022-02-02 18:12:42,217 - octoprint.server.util.sockjs - INFO - New connection from client: 192.168.3.111
2022-02-02 18:13:42,344 - octoprint.server.util.sockjs - INFO - New connection from client: 192.168.3.111
2022-02-02 18:14:42,451 - octoprint.server.util.sockjs - INFO - New connection from client: 192.168.3.111
2022-02-02 18:15:42,645 - octoprint.server.util.sockjs - INFO - New connection from client: 192.168.3.111
2022-02-02 18:16:09,050 - octoprint.server.util.sockjs - INFO - Client connection closed: ::ffff:192.168.3.111
2022-02-02 18:16:42,859 - octoprint.server.util.sockjs - INFO - New connection from client: 192.168.3.111
2022-02-02 18:17:30,844 - octoprint.server.util.sockjs - INFO - Client connection closed: ::ffff:192.168.3.111
However, no response is ever received by the browser.
Additional information about your network (Hardware you are trying to connect to, hardware you are trying to connect from, router, access point, used operating systems, ...)
Network consists of a server (Ubuntu 20.04 LTS) & the raspberry pi with octopi.
The server has various docker containers, including one running dnsmasq and several running nginx reverse proxies.
The current nginx configuration for the reverse proxy for octoprint looks like this (note that the commented out bits are other things I've tried along the way):
server {
listen 80;
server_name octopi.########;
root /usr/share/nginx/html;
location /static/ {
proxy_pass http://octopi.lan/static/;
proxy_set_header Host $http_host;
proxy_set_header Upgrade $http_upgrade;
proxy_set_header Connection “upgrade”;
}
location / {
proxy_pass http://octopi.lan/;
proxy_set_header Host $http_host;
proxy_set_header Upgrade $http_upgrade;
proxy_set_header Connection "upgrade";
proxy_http_version 1.1;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Scheme $scheme;
# proxy_set_header X-Scheme $scheme;
# # Also tried: proxy_set_header X-Scheme https;
# add_header X-Served-By $host;
# proxy_set_header Host $host;
# proxy_set_header X-Forwarded-Scheme $scheme;
# proxy_set_header X-Forwarded-For $remote_addr;
client_max_body_size 0;
auth_basic "Restricted Content";
auth_basic_user_file /etc/nginx/.htpasswd;
}
location /.well-known {
}
}
All of this sits in a docker-compose set including letsencrypt-proxy-companion to make it all be https nicely. The /static location was added because I had errors in the javascript console about permission denied accessing manifest.json.
I currently have no reverseProxy section in config.yaml, but previously I have also tried adding this:
reverseProxy:
prefixHeader: X-Script-Name
schemeHeader: X-Scheme
hostHeader: X-Forwarded-Host
For reference, this nginx configuration (for nextcloud) works perfectly, as do several others (some of which have basic auth):
server {
listen 80;
server_name nextcloud.###########;
root /usr/share/nginx/html;
client_max_body_size 20G;
location / {
proxy_max_temp_file_size 0;
proxy_pass http://##########:8888/;
}
location /.well-known {
}
}
 Warning
Warning